Tech bytes
Build a low cost wifi bridge or repeater
I have my broadband router installed in dining area and my study is a bit far from there. I needed LAN ports in study to connect CCTV DVR and a Linux server. I didnt wanted to extend network in another room using LAN cable. So I was looking for a low cost wifi router which […]
Delete old data in Elasticsearch
ELK platform provides great solution aggregating and indexing various log, events within a organization. But you may not want to keep old data in Elasticsearch forever. Also see ELK installation and configuration To delete old data you can use “elasticsearch-curator” tool You can simply install it as $pip install elasticsearch-curator Followed by some basic configuration. […]
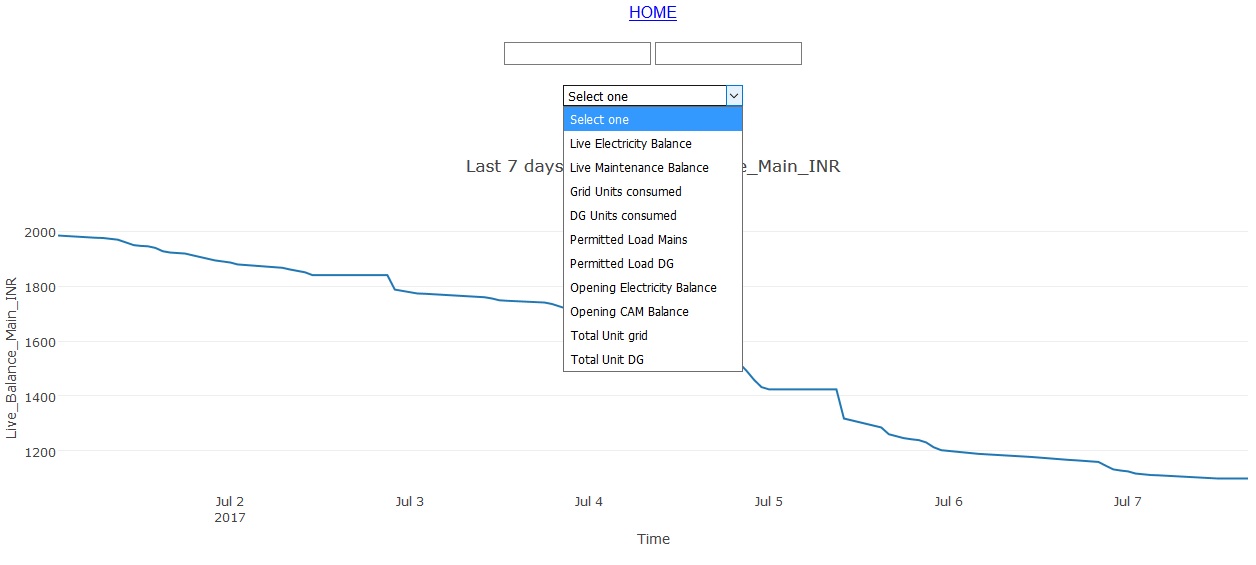
Realtime monitoring of apartment electricity and maintenance
These days many private housing complexes are providing pre-paid system for electricity and other charges. In our society we have similar arrangement. But there is lack of transparency and sometimes service provider tend to deduct amount for no reason or they charge for generator power consumption while grid supply was available. To monitor such situation […]
Syslog and snmp traps in ELK – Taming ELK
ELK stack is quite capable solution for event, logs, data aggregation and parsing. It offers a very shiny yet highly flexible web frontend. You can extend it to limits you can think off. It is a perfect open source tool for end to end data analytics.So what is ELK exactly ? ELK is composed of […]
Linux High availability quick setup
Consider two Linux machines: Active machine heart beat IP: 192.168.1.1 Passive machine heart beat IP: 192.168.1.2 Virtual/Floating IP 192.168.2.11 Install heartbeat software on active and passive machines manish@active-mc:~$ aptitude install heartbeat manish@passive-mc:~$ aptitude install heartbeat Get node names of both machines manish@active-mc:~$ uname -n active-mc manish@passive-mc:~$ uname -n passive-mc On Active host do following Configure […]
SSL certificate for websites and other applications
In order to obtain SSL certificate you have generate certificate signing request file(CSR) and a private key. Then you send CSR file to signing authority who will then generate and deliver SSL certificate using CSR file. Never leak out private key to anyone, not even signing authority. CSR holds information like domain name, country, city, […]
SQLite Basic tutorial
SQLite is a relational database management system contained in a C programming library. In contrast to other database management systems, SQLite is not implemented as a separate process that a client program running in another process accesses. Rather, it is part of the using program. SQLite is ACID-compliant and implements most of the SQL standard, […]
Installing Linux on Pen drive – mobility OS
A really good option for people who use public PCs for internet and other jobs. but for me I need Linux on pen drive because my company doesn’t allows users to install Linux on office laptops. You can really enjoy power of Linux anywhere anytime with this solution. Its simple, easy and handy. All you […]
Altina GBT709 Bluetooth GPS receiver
What is GPS? The Global Positioning System (GPS) is a satellite-based navigation system made up of a network of 24 satellites placed into orbit by the U.S. Department of Defense. GPS was originally intended for military applications, but in the 1980s, the government made the system available for civilian use. GPS works in any weather […]
DSL and WiFi security tips for home internet users
Recently in India investigating agencies have found militants using WiFi access points of home users to send threat mails. and ultimately investigation is focused on owner of WiFi DSL connection. well this could happen with any one of us who is using DSL with WiFi. How is this tracked ? when a hacker connects to […]